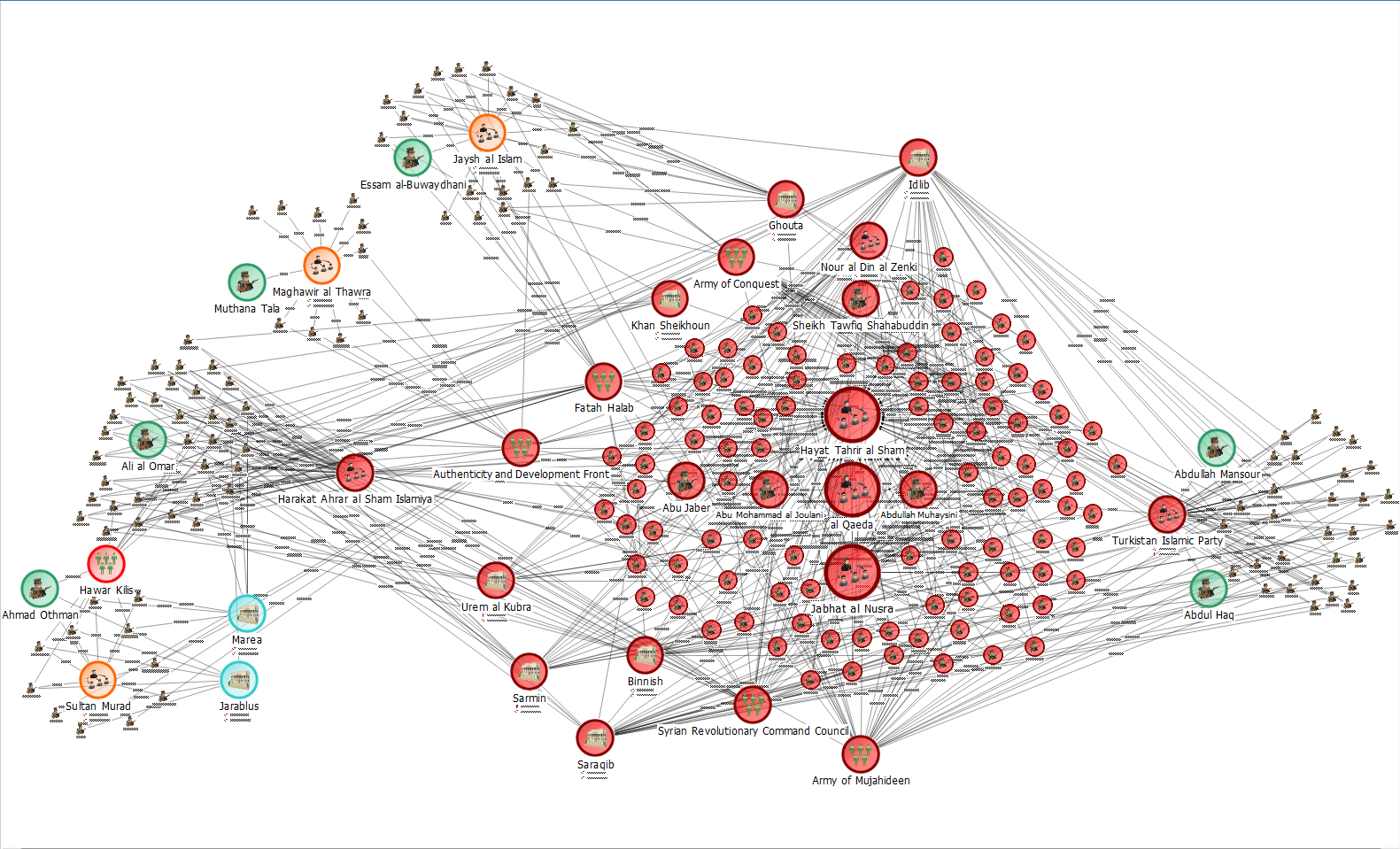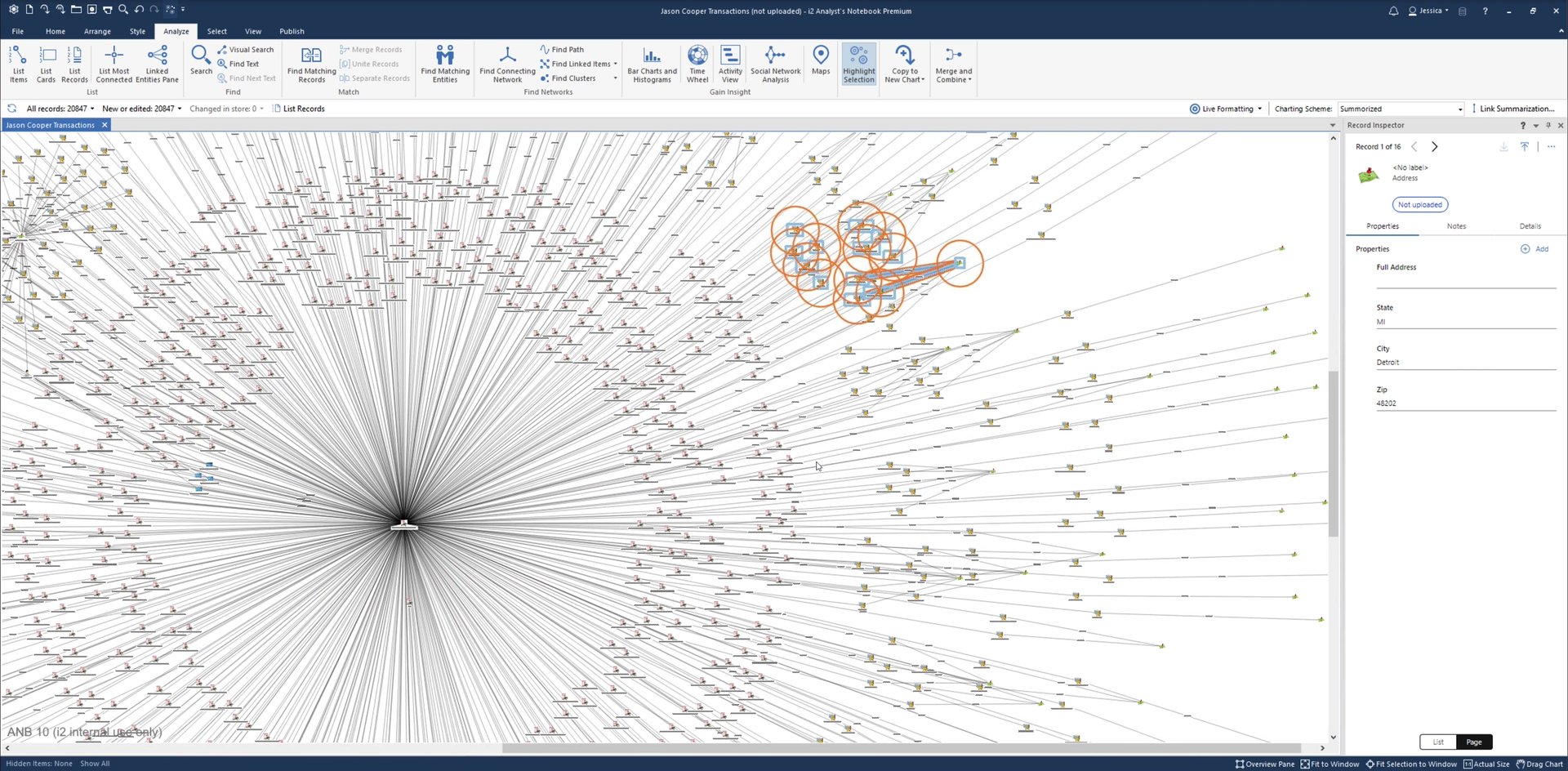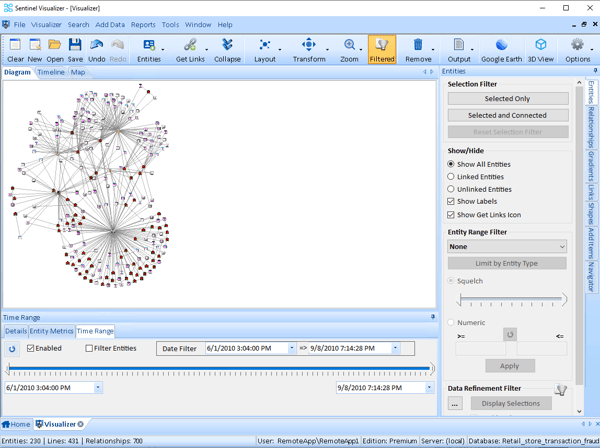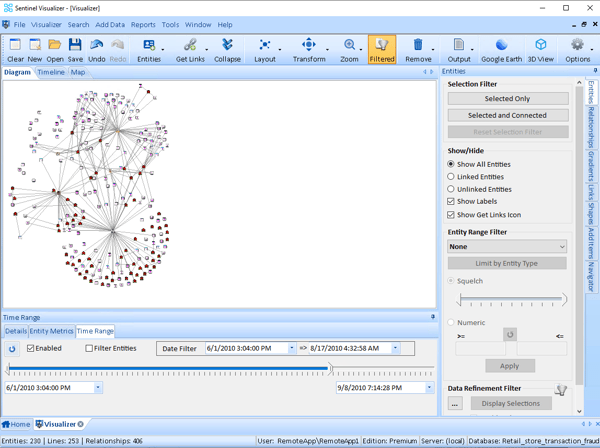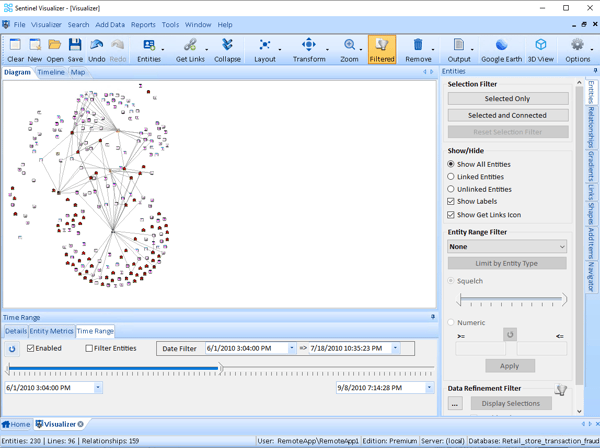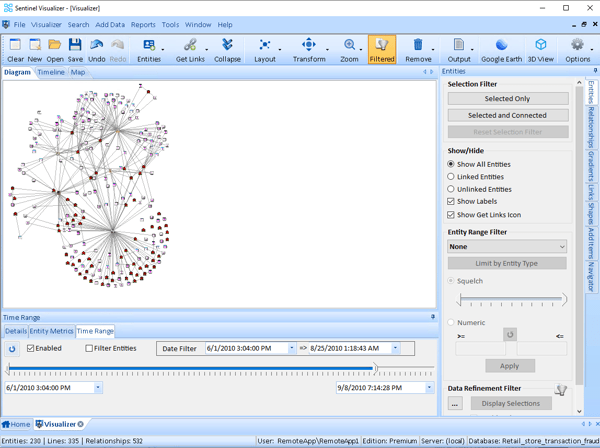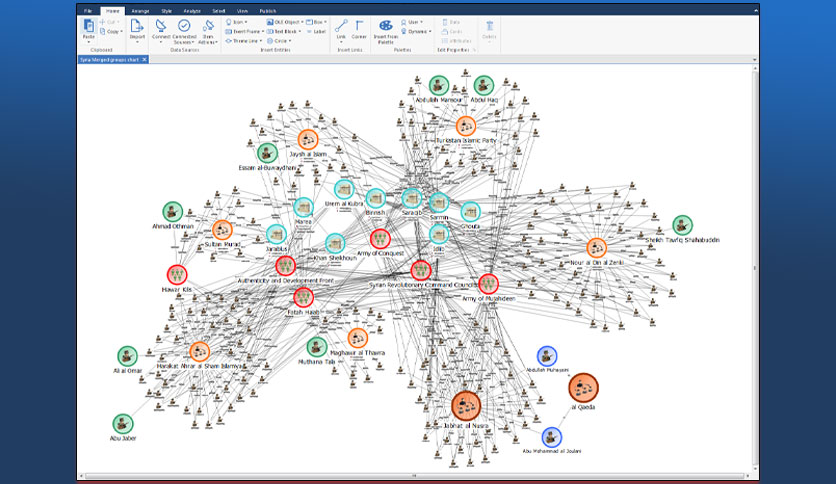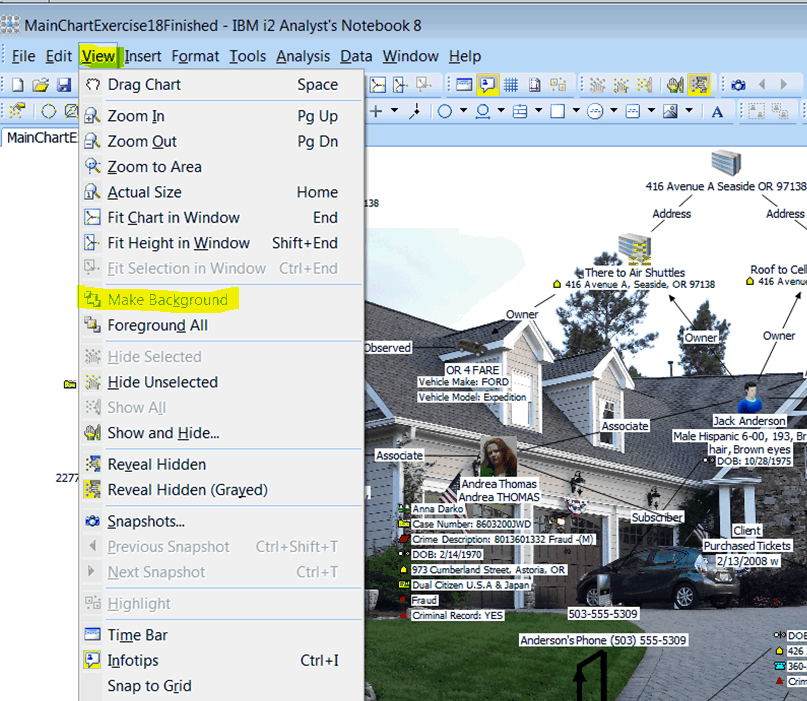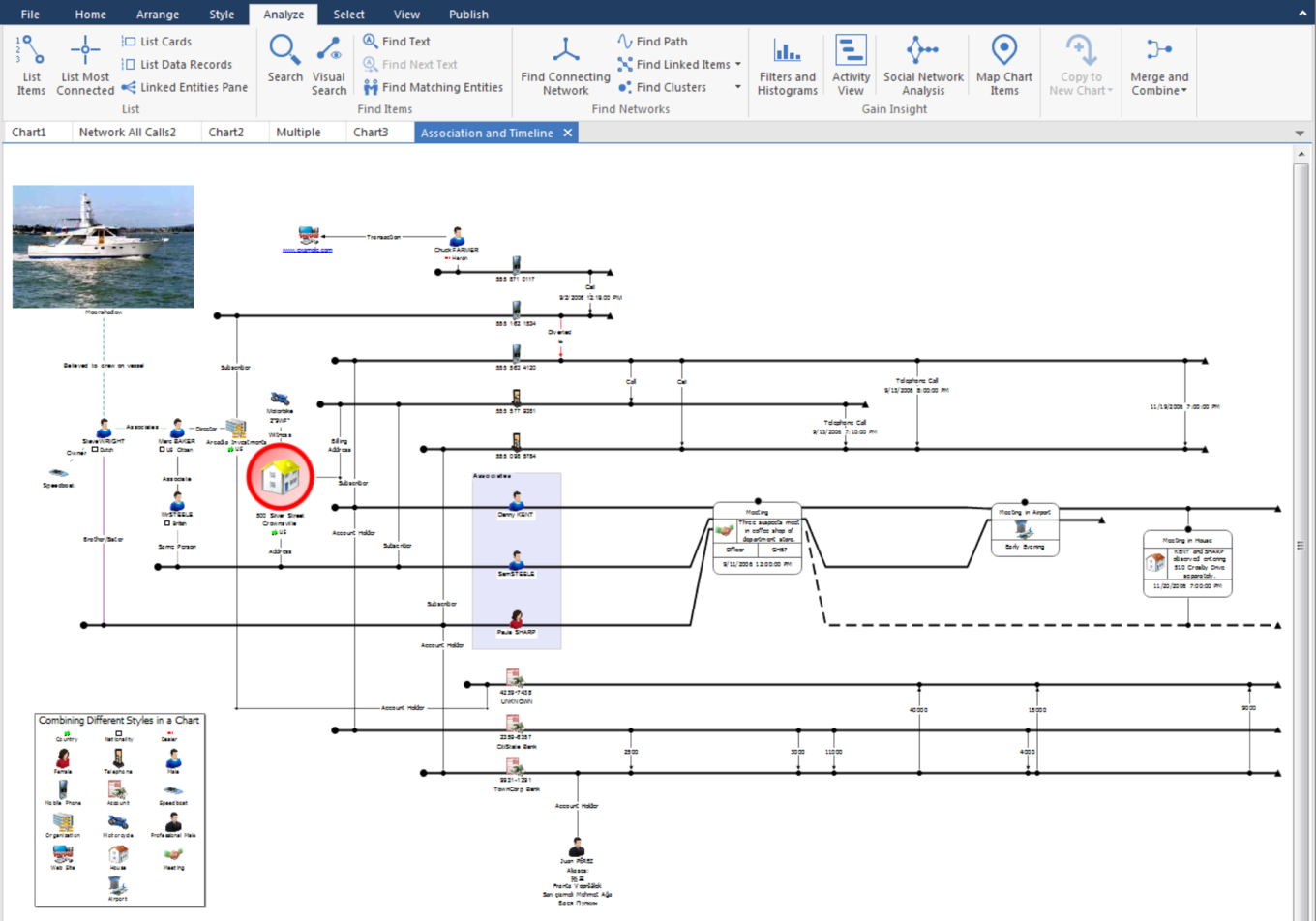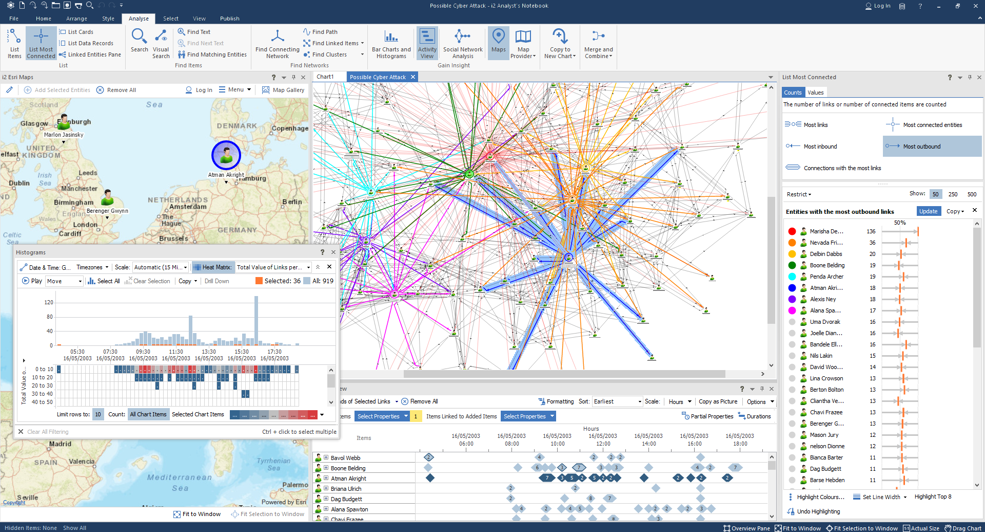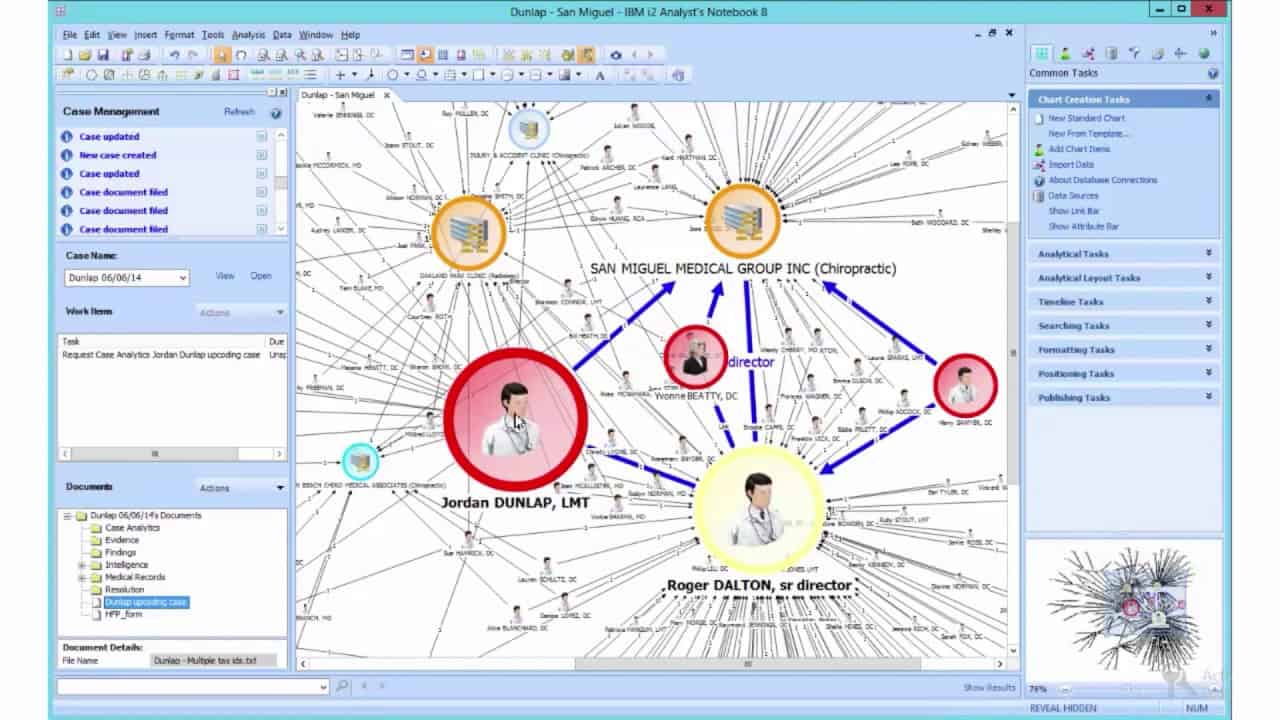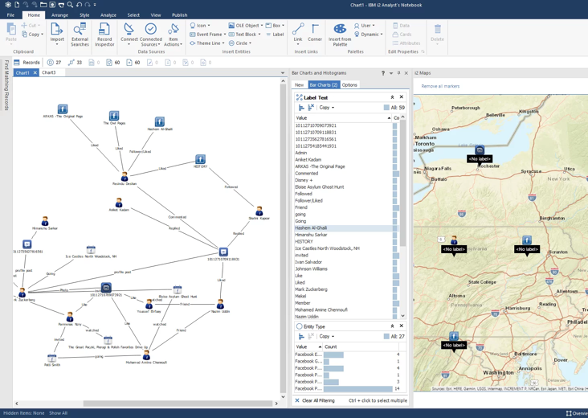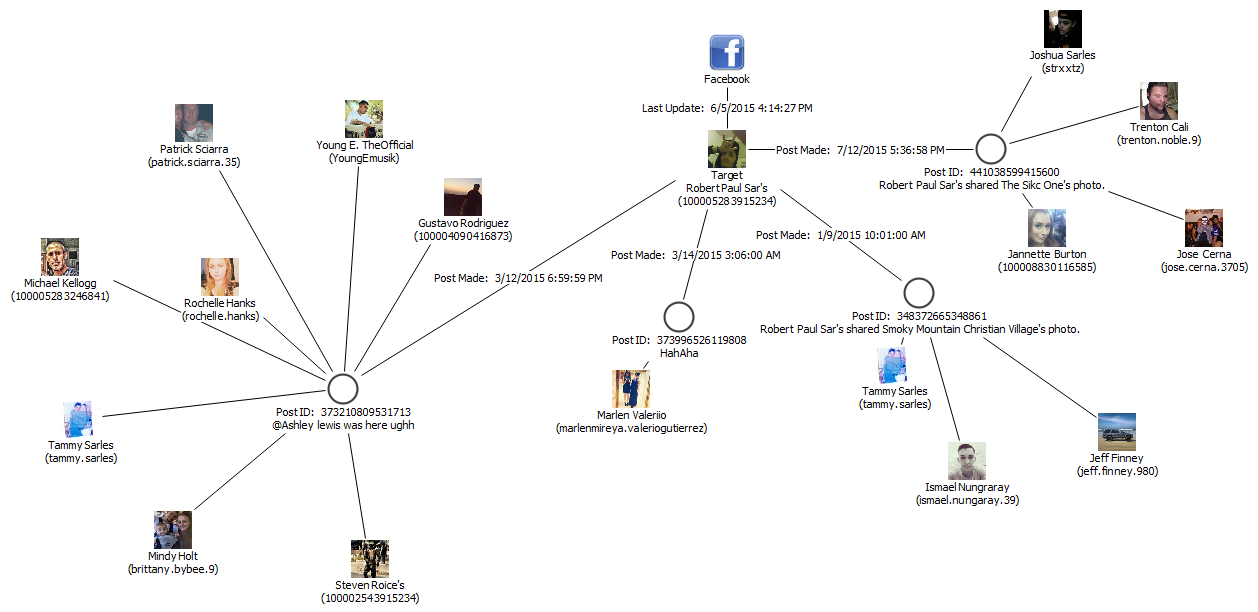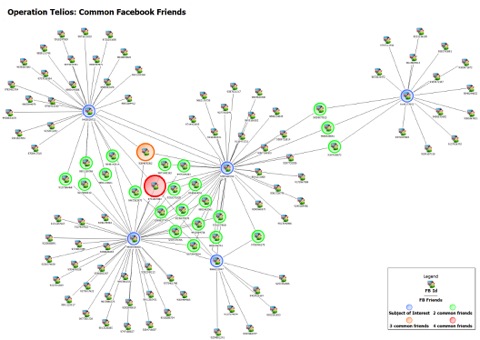
X 上的 Futurum Global:「We provide specialist intelligence analyst, #CrimeAnalyst and targeting #analyst training, including IBM i2 Analyst Notebook. Our training also includes social media, open source, and Internet exploitation and analysis (#SOCMED, #

PAMECA V | “i2 Analyst's Notebook” PAMECA V organized a five-day online training course on “i2 Analyst's Notebook” for eight analysts of the Central Investigation Directorate and Tirana Local Police Directorate, on